PROS Cloud
Secure cloud solutions you can rely on.

With a broad range of offer and pricing optimization solutions, PROS Cloud applications provide powerful capabilities to help you achieve your business goals with confidence.
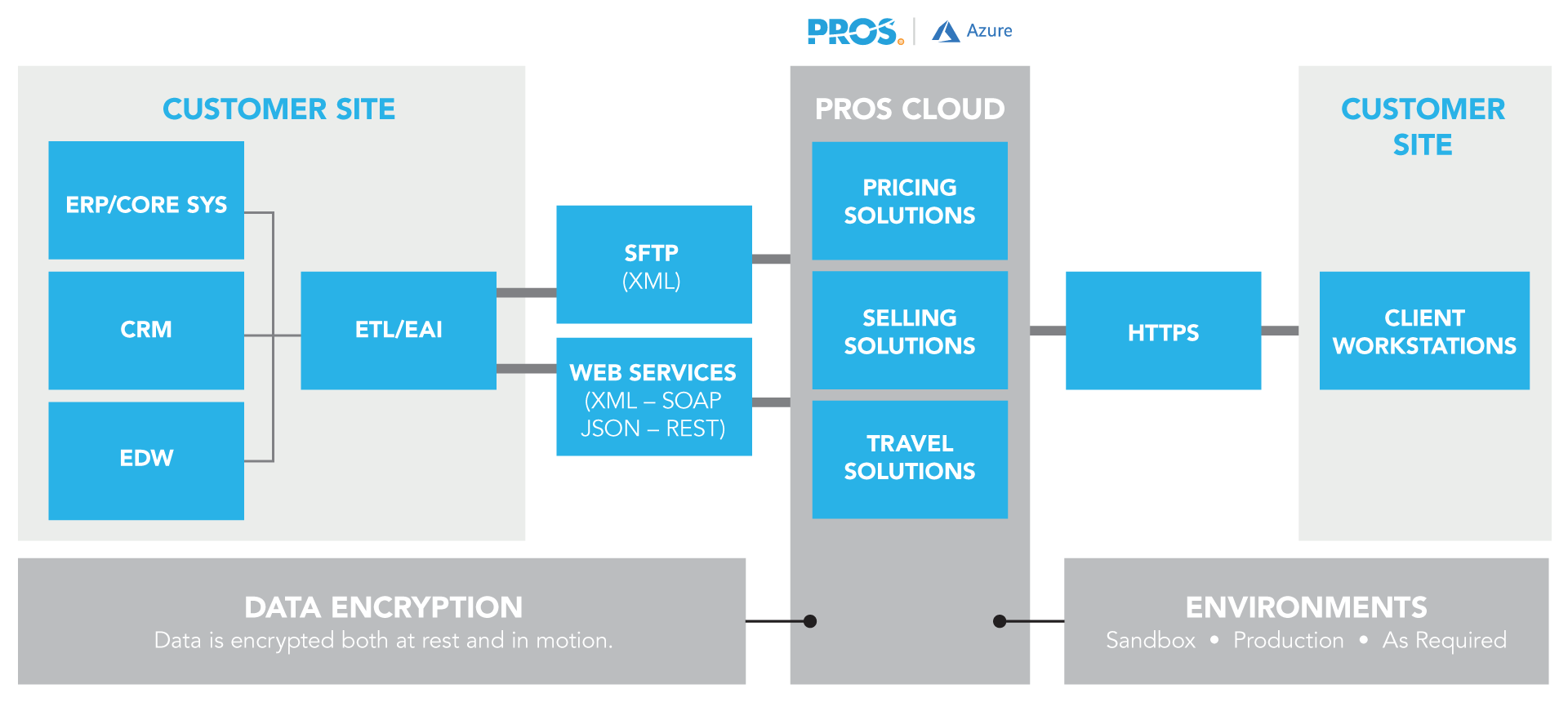
PROS Cloud Architecture
The PROS Cloud is delivered globally under a Software-as-a-Service (SaaS) model hosted on Microsoft Azure.
For a subscription fee, PROS provides access to PROS applications via a secure internet connection. This approach frees your IT team from the challenges associated with managing, maintaining and funding a scalable, secure and high-performance IT infrastructure.
The PROS Cloud communicates securely with your existing IT infrastructure over HTTPS.
In a modern enterprise IT setting, there will often be multiple IT system environments in use. PROS can provide environments to match your unique needs.
PROS Cloud Schematic
Secure Data Centers Worldwide
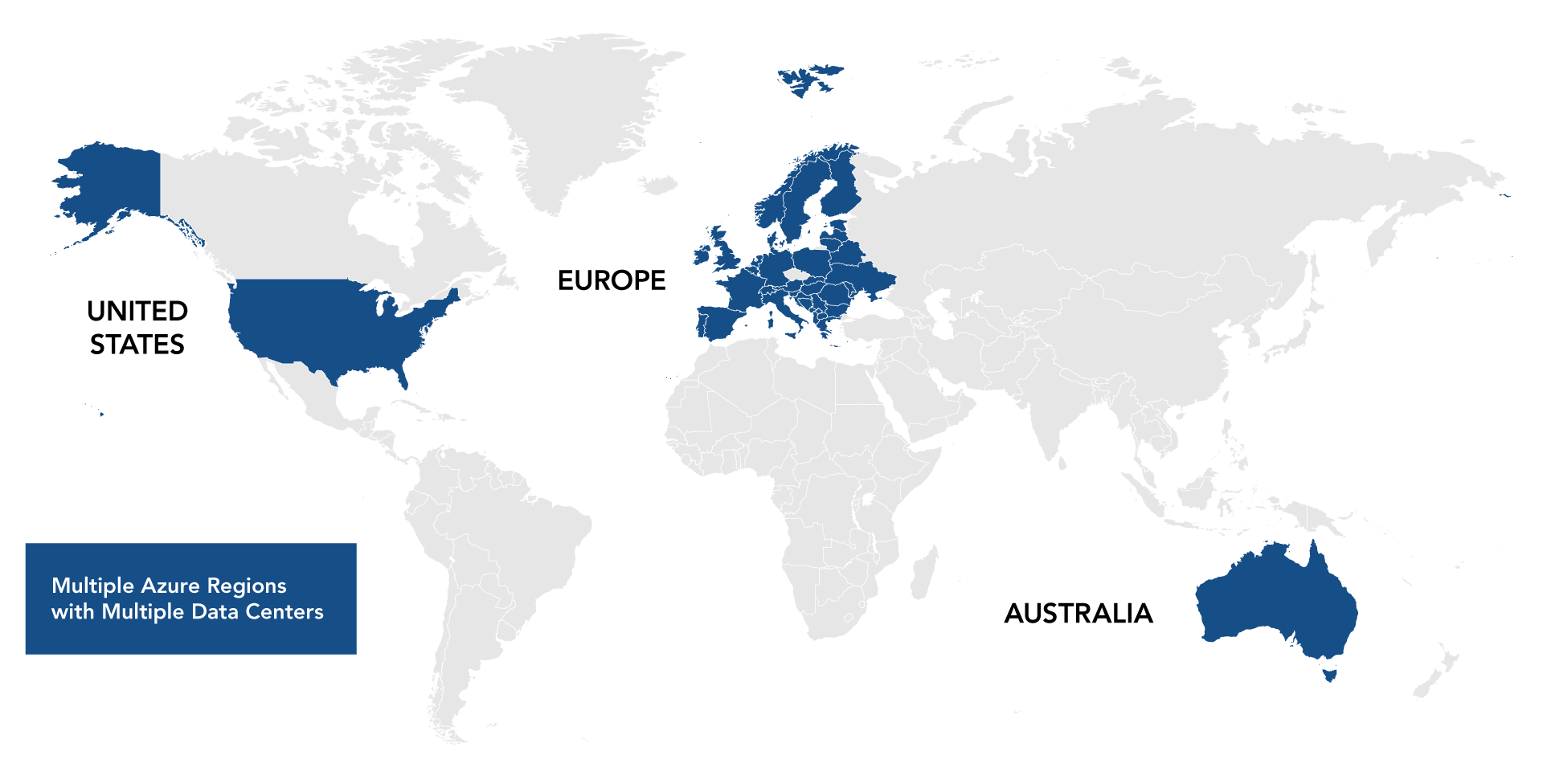
PROS positions its data centers in optimal geographic locations to minimize latency and observe local legislative requirements. We utilize strategically positioned data centers within the Global Microsoft Azure network.
PROS data centers are deployed in primary and secondary pairs for backup and failover.
There are currently PROS data center pairs in the Americas, northern and central Europe, and Australia, with further locations planned.
We regularly evaluate data center expansion to enhance services for our global customers.
Scalability, Elasticity, and Resilience
PROS Cloud is built on Microsoft Azure and specifically configured with elasticity to scale to meet your performance requirements. We’ve architected our SaaS solution to be highly available:
- Azure’s hyperscale data centers offer a wide range of resilient, secure, compliant, performant, and sustainable services.
- Secondary data centers receive data backups.
- A secondary data center is located at least 150 miles (240 km) away from the primary for high availability.
- There is automated failover from the secondary data center in event of primary data center loss.
The PROS Cloud team performs weekly full and daily incremental backups. PROS has a defined Recovery Point Objective (RPO) and Recovery Time Objective (RTO) for each solution. Scheduled backups are audited regularly and restore functionality is tested periodically to support disaster recovery planning.
Product support is a vital part of the total PROS customer experience. We’re dedicated to ensuring issues are resolved to your full satisfaction. Contact your PROS representative for details on our suite of product support offerings.
Responsive Operations and Support
PROS provides two responsive global customer support centers for its Cloud Operations: one in Houston, TX, USA and one in the EU, Sofia, Bulgaria.
Rigorous approach
PROS Cloud environments are managed using industry standard processes.
We’re rigorous and responsive to ensure the health of your environments. When we plan to make changes to deployments, a detailed change request is created that includes the impacted environment, implementation, rollback, verification, and customer communication procedures.
DevOps
We operate on a DevOps support model, so all the business functions that design, develop, deploy and support PROS solutions are in a single, coordinated organization.
Proactive support team
The PROS Cloud operations support team monitors systems activity to predict peaks in demand and then responds quickly and decisively to minimize operational impact.
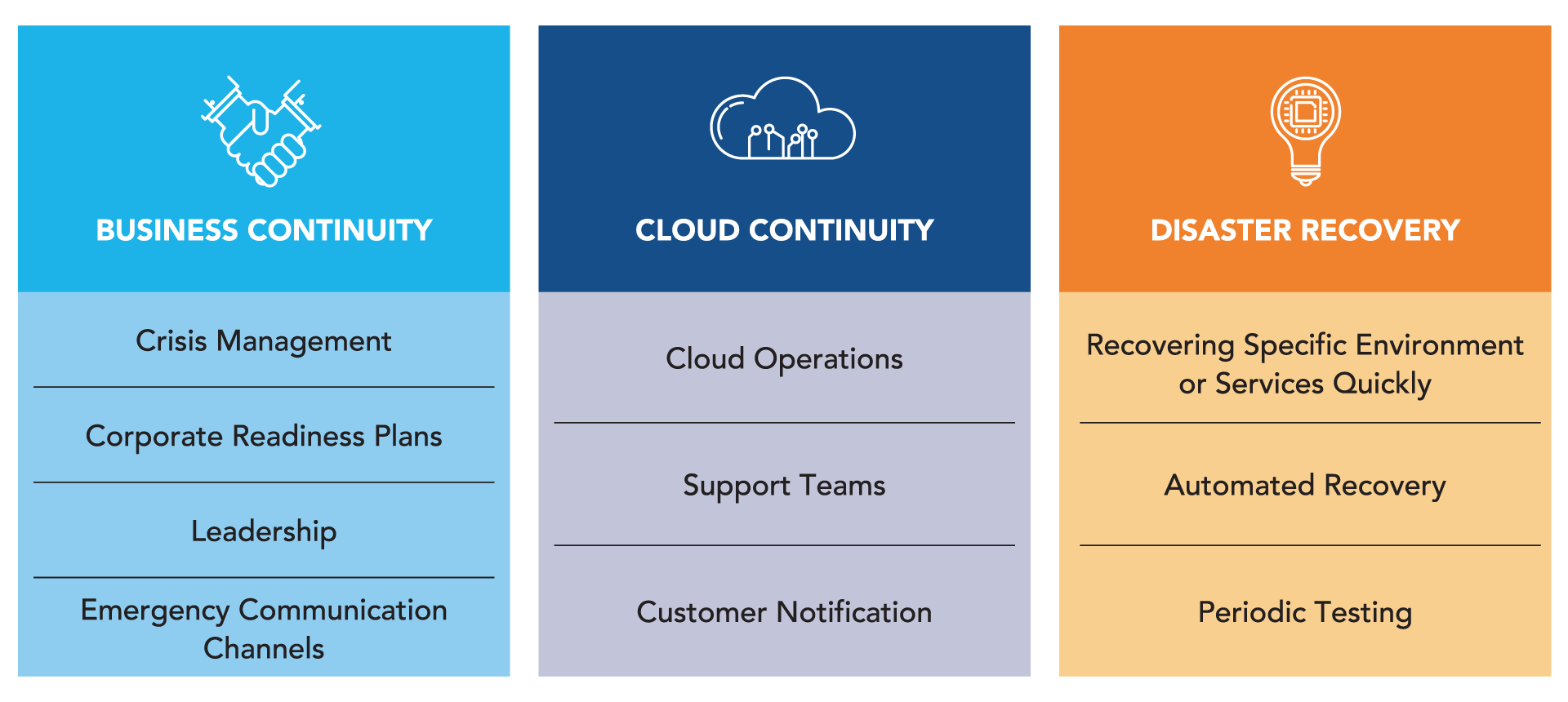
Disaster Recovery Overview
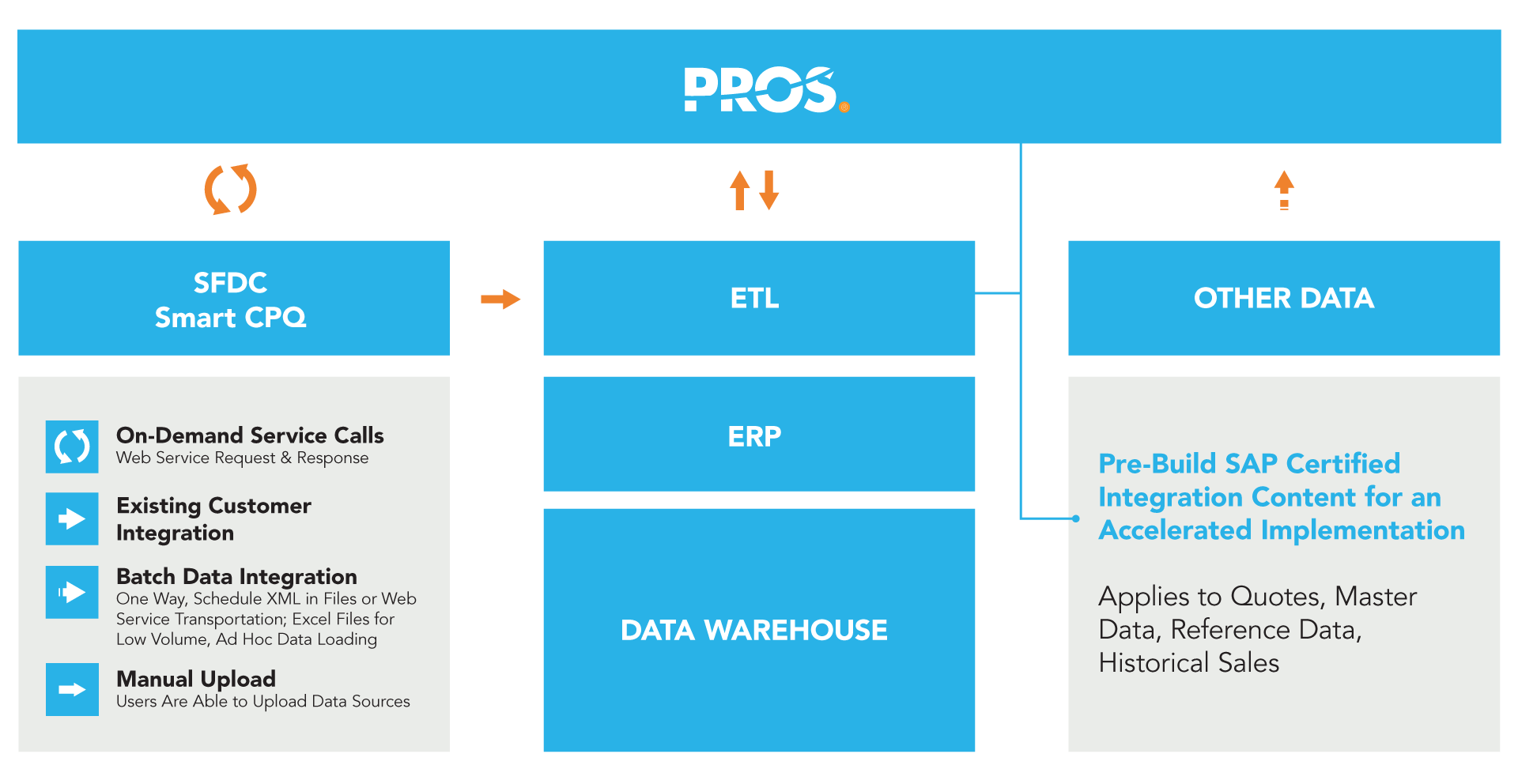
Flexible Integration
Our solutions are integrated to your enterprise business systems, such as ERPs and CRMs. PROS works with many different systems –even those that have been heavily customized to meet customer requirements. We offer a variety of integrations that help get you up and running quickly:
- Industry-standard web services (SOAP/REST) and XML move data between PROS and external applications.
- SAP-certified content for integration with SAP Process Orchestration and Integration tools.
- Microsoft Dynamics 365 and Salesforce CRMs data field-matching adapters for PROS Smart CPQ.
So who completes the integration activity? For maximum flexibility, it can be any combination of the following options:
- Your IT team
- PROS Customer Success team during implementation
- PROS Integration Service
- PROS Certified System Integrators
Typical PROS Solution Integration Landscape
Security Management Program
Certifications and compliance
Security is central to PROS culture. PROS is compliant with the General Data Protection Regulation (GDPR) and we annually undergo independent third-party audits for compliance with:
- SSAE16 SOC 2 Type 2
- ISO 27001
- ISO 27018
- Cloud Security Alliance’s Cloud Control Matrix
Threat protection programs
We have an established security program to protect the confidentiality and integrity of information and services from anticipated threats of unauthorized or unlawful disclosure, modification, loss, or destruction of information. PROS Security Council performs regular gap assessments and executes initiatives to cover identified gaps.
Continued enhancement
PROS solutions are subject to continual development to protect and enhance your investment. Functionality patches and minor enhancements are released and applied monthly while version upgrades occur every two months. Security patches are applied quickly to address any potential gaps.
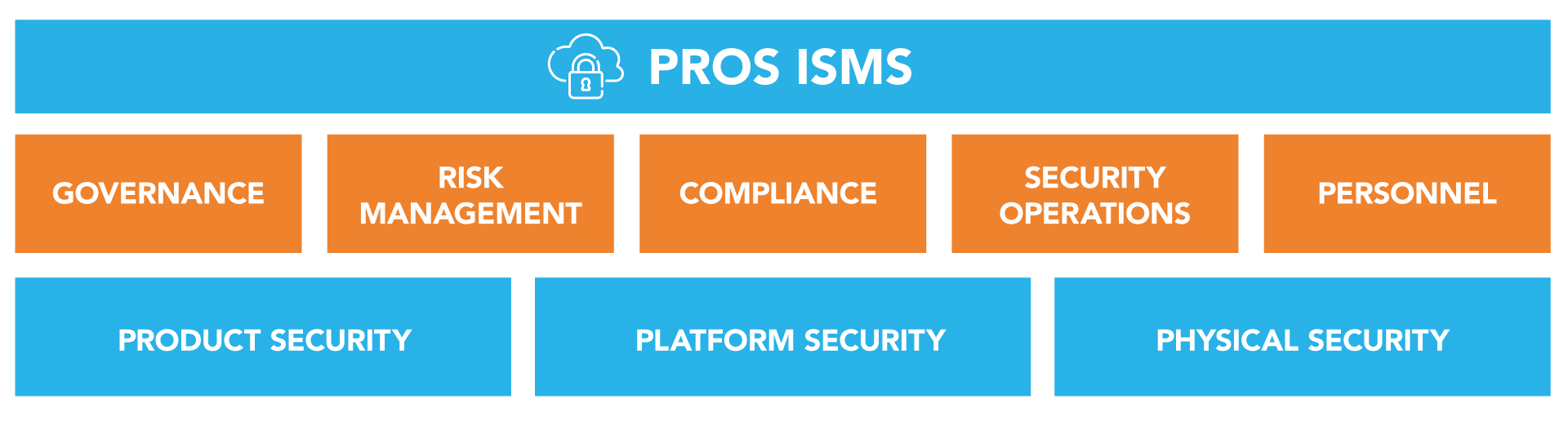
PROS Information Security Management System
The PROS Information Security Management System is governed by a Security Council responsible for oversight and enforcement of comprehensive written security policies specifying:
- enterprise-wide security awareness training
- logical and physical security access control
- environmental and physical security
- vulnerability management
- incident response & disaster recovery; and more
The PROS Information Security Management System was designed and implemented in alignment with the requirements of ISO 27001. It includes policies, standards, guidelines and procedures for managing PROS information security.
PROS Applications, Designed Securely from the Start
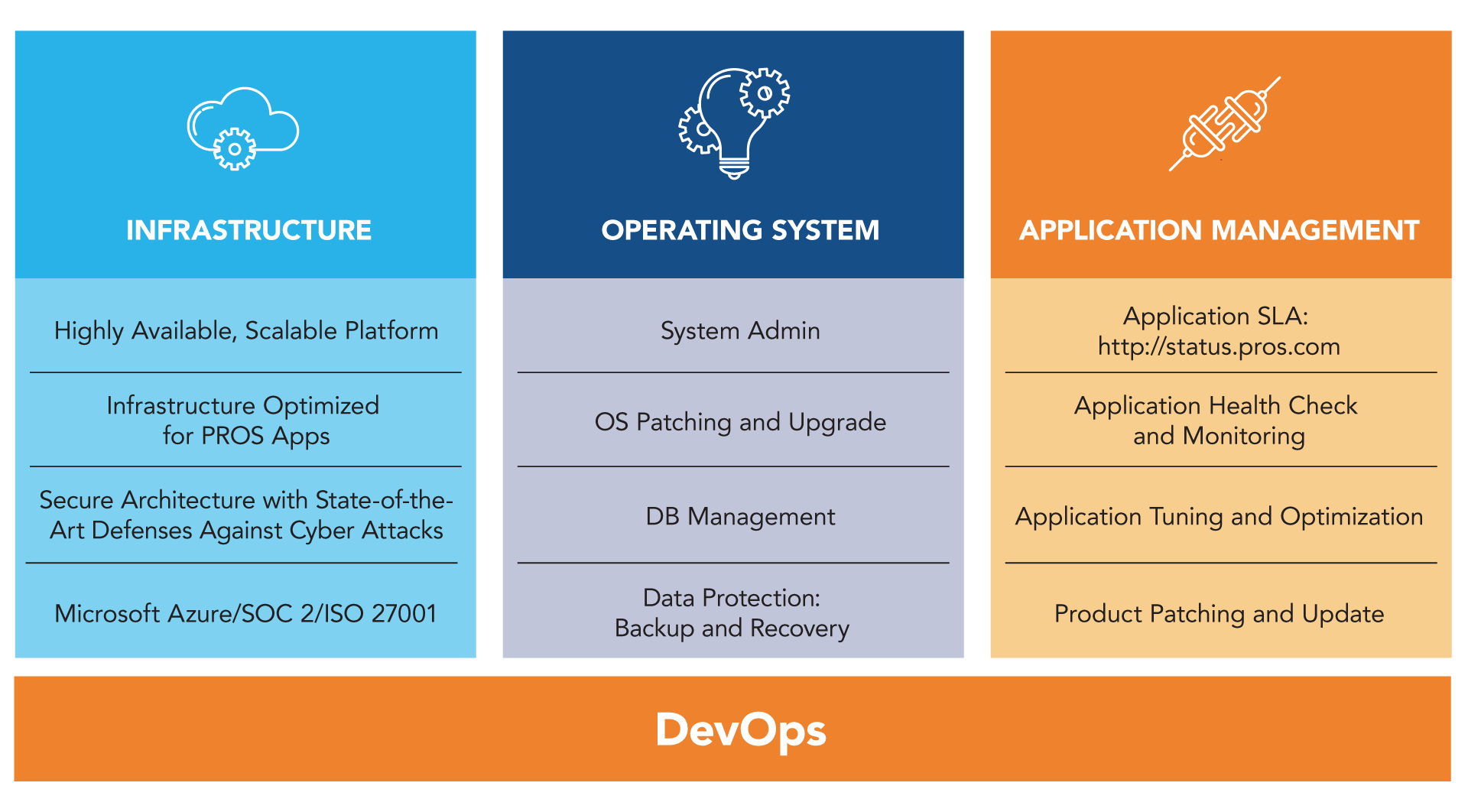
PROS SaaS Capabilities
PROS development teams utilize Secure Development Lifecycle (SDLC) processes and perform rigorous testing to ensure security.
- Base PROS SDLC on OWASP industry best practices and tailor to the Agile methodology.
- Perform Threat Modelling to identify and model security threats.
- Complete Static Analysis Security Testing at the code level to identify vulnerabilities early.
- Execute Dynamic Analysis Security Testing at the Web App level to identify vulnerabilities.
- Conduct Final Security Review of all security activities performed on the application prior to release.
- Run regular Vulnerability Scanning and manual Penetration Testing within the PROS solution.
State-of-the-art Security Infrastructure
PROS deploys a state-of-the-art network security infrastructure. We utilize firewall and Intrusion Prevention System technologies to analyze network traffic and guard against attacks. For Host Security, PROS deploys an advanced antimalware solution that uses a pure machine learning approach to determine malicious activity. The solution can detect threats without relying on signature-based technology and techniques. A sophisticated host-based incident response tool hunts and captures threat activity in almost real time in conjunction with a powerful tool that can model and track the introduction of known good changes in systems and protect from non-trusted changes.
User Authentication
PROS Best Practice approach for installations is to leverage our customers’ current corporate identity management solution. Single Sign On (SSO) is the PROS preferred method. Where an SSO approach is used to integrate to an existing application infrastructure, we can leverage the Security Assertion Markup Language standard (SAML 2.0) as well as Microsoft Azure Active Directory.
Data Encryption
All data at rest is encrypted with an AES 256bit cipher. Data in motion is sent over HTTPS and TLS 1.2 where possible and again encrypted with an AES 256bit cipher. Encryption keys are held and protected as per key management best practices.
